It’s A Secret

Do you use code when you text or in your emails?
B2B, CRM, RSS, CPM, BRB , URL, HIFW, HMB and ILY and the popular FYI – just some of the shorthand we use in business and social media when communicating. We’ve become accustomed to use abbreviations to communicate, saving us time in our texts and notes. Now, I’m not much of a social media guy, but I must admit when talking, texting, emailing with Jackie or my girls, I’ll throw in a little of my own shorthand now and then. But IMHO, with all the stories in the news about social media and different crypto currencies, I thought it would be cool to investigate stories about the use of code throughout the ages. (keep in mind, I am always a little concerned when someone asks me up front if they can be honest with me – really???) TBBH, some of the abbreviations I’ve heard of and others new to me. Enjoy, and feel free to come up with your own abbreviations – hey, YOLO. TX to google, chat.ai and sproutsocial.com for the info.
Top 130 Social Media Abbreviations and Slang: CLICK HERE
Remember, sometimes it’s easier to just pick up your phone and call!
Codes have played a pivotal role in shaping history, from military strategies to secret messages to computer languages. They’ve been used to transmit vital information, protect sensitive data, and even spark intrigue. Here are some of the most famous codes throughout history that have left an indelible mark on our world. And when you figure out how crypto works, give me a call.
- Ancient Encryption – In 49 BC, Julius Caesar employed a simple yet effective encryption technique known as the Caesar cipher. He was the mind behind an early documented use of simple substitution ciphers – the one that would eventually bear his name, called for shifting alphabet letters. Letters were shifted three places ahead; in English, that means an A becomes a D, B becomes E, etc. shifting each letter of the alphabet a fixed number of places down or up the alphabet to encrypt his military messages. It may seem like child’s play compared to the more complicated codes that later emerged, but the Caesar Cipher worked, as it was easy for allies to remember, confounded the largely illiterate hordes who resisted intrusion, and allowed Caesar to significantly expand the Roman Empire.
- The Great Cipher – Developed by a father-son team that encrypted messages for the French monarchy in the 17th century, the Great Cipher repelled all attempts at penetration until military cryptanalyst Étienne Bazeries unlocked its secrets some 200 years later. As described in Simon Singh’s The Code Book, Bazeries broke through when he realized the cipher’s 587 unique numbers generally represented syllables, though he remained hindered by the built-in traps; some numbers did stand for individual letters, while others served to delete the previous number. Bazeries’ success enabled historians to read letters dated from the reign of Louis XIV, with one seeming to point to the identity of the infamous Man in the Iron Mask as a disgraced military commander named Vivien de Bulonde.

The WWII Enigma Machine.
- World War Wonder – After the conclusion of World War I, the German military began laying the groundwork for future conflicts with the development of a typewriter-like contraption that generated an ever-changing system of encrypted messages. Said to have been named for Elgar’s Variations, the Enigma Machine enabled users to type in letters that wound through a series of interior rotors before spitting out different letters. The recipient of a coded missive would adjust his machine’s rotors to the same position, enabling him to read the original message. This electro-mechanical device was used to encrypt messages, but a team of mathematicians and cryptanalysts at Bletchley Park, including Alan Turing, cracked its complex code, helping the Allied forces decipher crucial messages during World War II.
- Unbreakable Tongue – In another World War II tale, the Navajo Code Talkers used their native language to create an unbreakable code. The Navajo language’s complexity and lack of written form made it incredibly difficult for enemies to decipher. These Code Talkers played a crucial role in transmitting sensitive information, confounding enemy codebreakers, and proving the value of indigenous languages in cryptography.
- The Zodiac Killer – In the late 1960s and early 1970s, the Zodiac Killer terrorized California with a series of murders and cryptic letters to newspapers. He included ciphers that he claimed would reveal his identity. One of these ciphers, known as the “Z340,” remained unsolved for over 50 years. In 2020, a codebreaking team finally cracked it, revealing the chilling message of the killer.
- RSA Encryption – In the 1970s, Ron Rivest, Adi Shamir, and Leonard Adleman introduced the RSA encryption algorithm, which revolutionized digital security. RSA relies on the mathematical difficulty of factoring large prime numbers, making it extremely secure for transmitting sensitive data over the internet. This asymmetric encryption method forms the foundation of modern secure communications and helped programmers to assemble the sophisticated block chain used in crypto.
- Voynich Manuscript – The Voynich Manuscript, dating back to the 15th century, is a mysterious book filled with elaborate illustrations and an unknown script. Despite decades of efforts by linguists and cryptographers, the manuscript’s content and purpose remain unsolved. The complex and unique nature of its code continues to captivate researchers, with its secrets yet to be fully unraveled.
- Information in Squares – QR (Quick Response) codes, developed in the 1990s, are a modern incarnation of encoding information. Initially used to track automotive parts. The codes have become ubiquitous in advertising, packaging, and mobile technology as they can store various types of data, from URLs to text, making them a versatile tool for sharing information.
- Bitcoin’s Blockchain – While not a traditional code, the blockchain technology behind Bitcoin introduced a new paradigm of secure and decentralized record-keeping. Using cryptographic techniques, each block in the chain is linked to the previous one, creating a tamper-resistant ledger. This innovation laid the groundwork for the development of cryptocurrencies and has far-reaching implications beyond finance.

- AND, OF COURSE MY FAVORITE …. PIA, as in PIA JOBS! – PIA is shorthand for pain the @%$ jobs. It’s become a driving force for us here at KHT – combining the genius of my team in deciphering your most challenging thermal processing projects. So, keep in mind, when one of your parts is just not meeting standards, or its performance is keeping you up at night, GMAC (give me a call) and I’ll GRBTY as QAIC and to solve your most pressing jobs. TY.
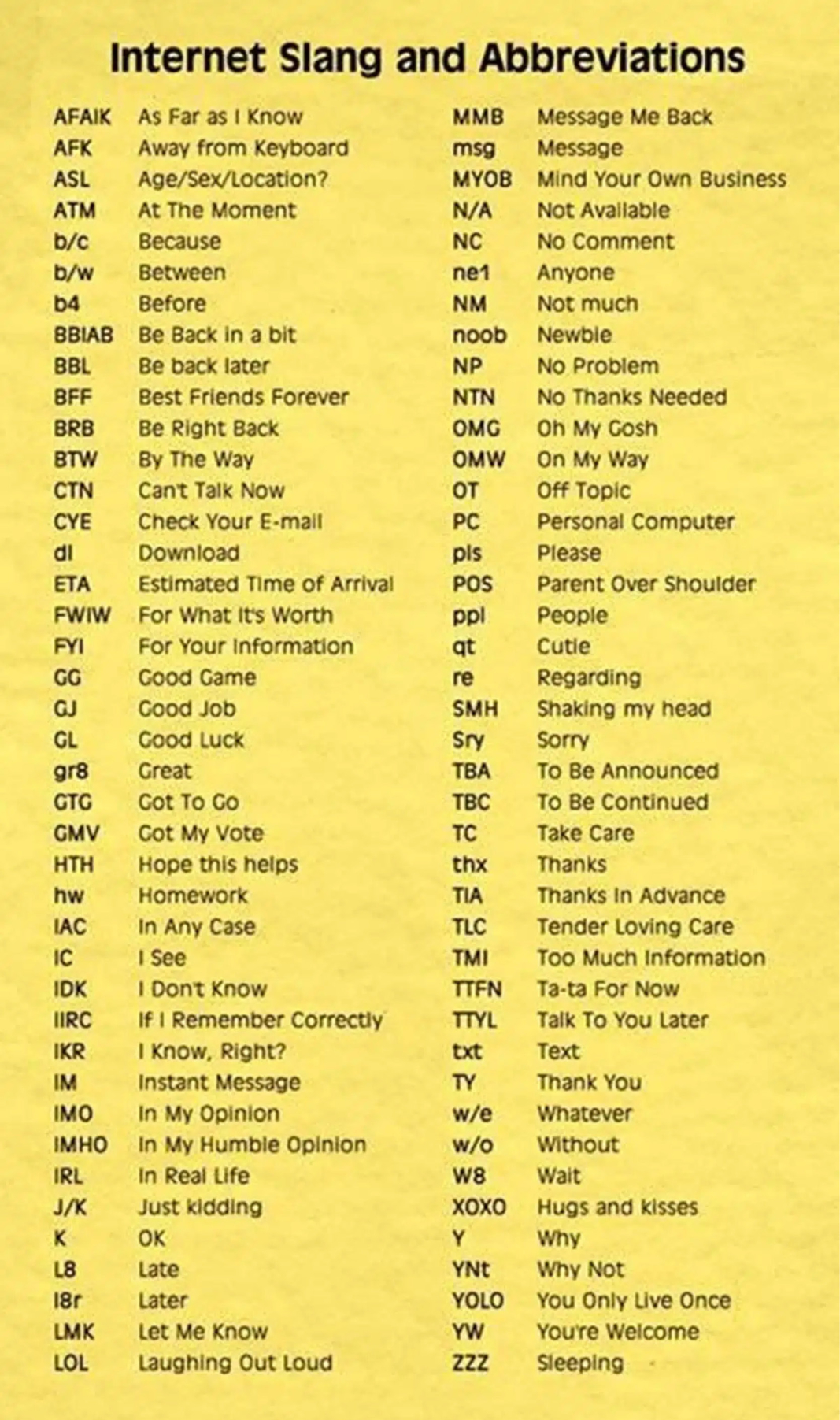
A primer for those needing help getting started or simply understanding what people are saying. :))))
::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
DO YOU LIKE CONTESTS?
Me, too.
As you may know the Kowalski Heat Treating logo finds its way
into the visuals of my Friday posts.
I. Love. My. Logo.
One week there could be three logos.
The next week there could be 15 logos.
And sometimes the logo is very small or just a partial logo showing.
But there are always logos in some of the pictures.
So, I challenge you, my beloved readers, to count them and send me a
quick email with the total number of logos in the Friday post.
On the following Tuesday I’ll pick a winner from the correct answers
and send that lucky person some great KHT swag.
So, start counting and good luck!
Oh, and the logos at the very top header don’t count.
Got it? Good. :-))))
Have fun!!
::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::


